
Breaking News: NordVPN, VikingVPN and TorGuard Have Been Breached by Hackers
According to some users, NordVPN became unsafe a few hours ago, with various browsers starting to block any connection to NordVPN because of expired TLS certificates.
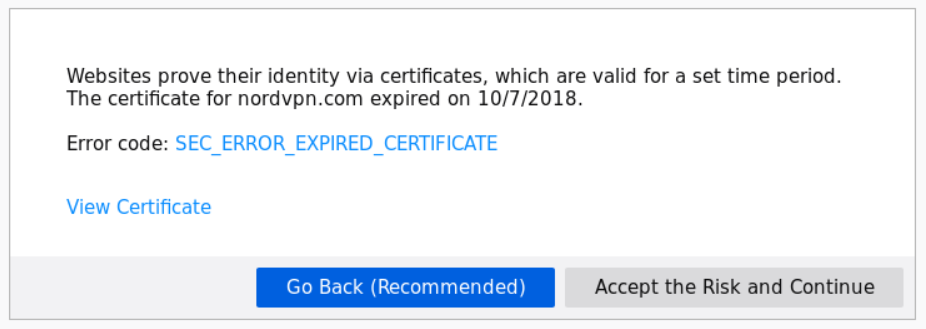
When accessing the NordVPN website with Firefox:
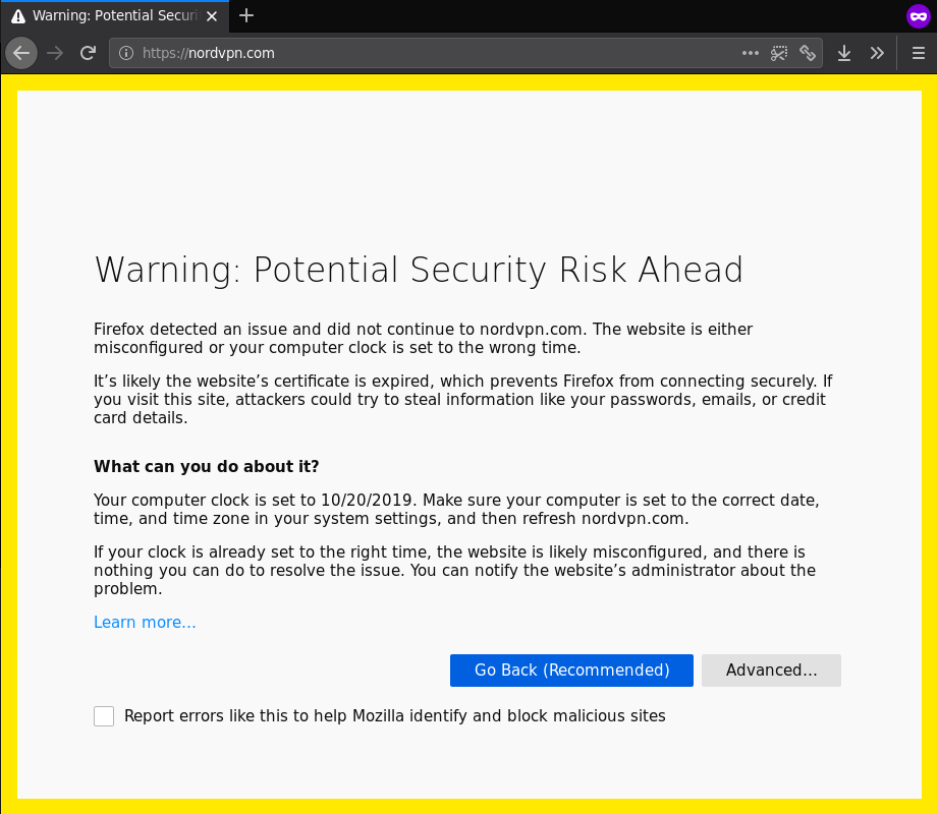
Apparently, the expired TLS certificates for NordVPN have leaked. This means that now anybody can setup a server with those keys. The screenshot below shows that someone has set up a server with a page that stated “this is not NordVPN”. This was quickly removed by the company.
This happened hours after the company published a tweet, now deleted, stating “Ain’t no hacker can steal your online life (if you use VPN). Stay safe”. A hacker then published on 8chan, a notorious message board, hacks to NordVPN and VikingVPN, both of which “weren’t practicing secure PKI management”, as well as TorGuard.
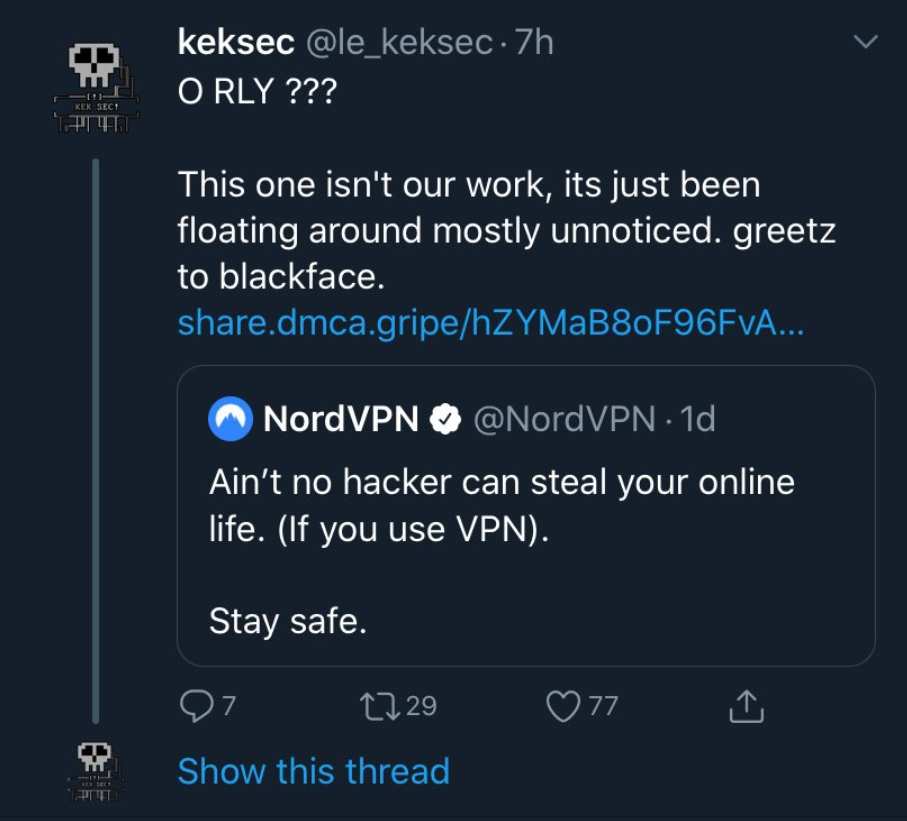
An official statement has not been made from any of the companies yet. NordVPN replied on Twitter:
It’s still not fully clear what happened and what the extent is of the breach, but one thing’s for sure: do not use NordVPN, VikingVPN and TorGuard until public statements from the companies have been made. As of now, these VPNs are not safe to use.
We will keep you posted as the story develops.
PS. we have dropped NordVPN from position 2 to 3 in our VPN rankings. We have no doubt that NordVPN will come out stronger from this safety breach – but for the time being 5 Euro VPN and ExpressVPN remain our safest options.
UPDATE 1: 2019-10-21 6:17 pm
After hours of speculations, NordVPN has put out a public statement that explains in detail what happened. Apparently, in January 2018 the company rented a server from a data center that did not meet the highest standards in terms of security. These servers were accessed on 20th March 2018 with no authorization “by exploiting an insecure remote management system”. During this attack, the expired TLS key was taken as well.
Anyway, according to the Panama-based company, the server did not contain any activity log, nor the attacker could have gathered any information regarding username and passwords, since “none of our applications send user-created credentials for authentication”. Furthermore, the key could have not been used to decrypt the VPN traffic of any other server.
The statement goes on to explain that after NordVPN had learned about the incident, they immediately terminated the contract with the server provider and that they feel confident that any and all users’ data were and still are safe and sound.
The official response reads: ”No user credentials have been intercepted. No other server on our network has been affected. The affected server does not exist anymore and the contract with the server provider has been terminated”.
NordVPN is now “taking all the necessary means to enhance the security”. As they state, they maximize the security of every aspect of their service, and they plan on launching 2020 an independent external audit of all their infrastructure.
Apparently, though, VikingVPN rented the same server from the same company, so the breach affects them as well. Depending on how they handle security, the conclusion that all of their users’ data is safe might not be true for them.
So, if the company statement is true, using NordVPN will not put you at risk of being attacked. Still, we suggest you be very cautious in using VikingVPN and TorGuard as we wait for their public statement regarding the incident.
UPDATE 2: 2019-10-24 15:38 pm
In the wake of the NordVPN incident, the Panama-based company published a second statement to make sure that everybody knows that their services “are still amongst the safest”. In this article, they explain in detail what happened and what are the risks for their users.
Here is a quick overview:
Only one server was affected, out of the 3000+ available in NordVPN. The incident happened because of “poor configuration on a third-party datacentre’s part”. NordVPN was not notified of the incident until a month later. - No user credentials were affected.
The intruder could not have monitored traffic. The TLS keys were stolen and could be used to attack users one at a time, although “it would require extraordinary access to the victim’s device or network (like an already-compromised device, a malicious network administrator, or a compromised network)”. Something that’s extremely unlikely to happen. - As we said, two other VPN providers (who used the same data center) were affected.
- The affected server did not contain user logs.
NordVPN has also contacted all the affiliates to let them know that NordVPN’s level of privacy is still one of the higher among any VPN. And that it’s only going to get more secure since the company plans on doing a massive audit of all their servers and partners early next year.
We can only applaud NordVPN for its transparency and willingness to recover from this incident. Here at TechTypical, we will keep monitoring the situation for any developments.





Leave a Reply